OEG can work in concert with various anti-virus tools such as CLAM AV, McAfee and Sophos.
This post details the setup for McAfee.
In my example OEG and McAfee are installed on the same machine.

Copy the following .dat files from McAfee to OEG_Home/conf/plugin/mcafee/datv2
- avvclean.dat
- avvnames.dat
- avvscan.dat
You will have to create /mcafee/datv2 beforehand

Copy config.dat to OEG_Home/win32/lib

Copy mcscan32.dll to /win32/lib

Restart OEG
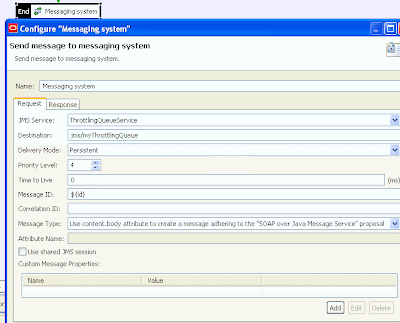
Create a Policy for VirusChecking –

Add the McAfee filter – configuring as follows

We are using the custom setting as we want to test with the EICAR test data -
checking the Scan for Test Files option.
For more on EICAR please refer to http://eicar.org/86-0-Intended-use.html
Add a Reflect filter
Add a relative path /VirusCheck
 Deploy and Test
Deploy and TestWe will use the EICAR test file to test the ant-virus filter.
http://eicar.org/86-0-Intended-use.html
Create a new .txt file (e.g. virusTester.txt) and copy and paste in the EICAR data
You may get the following message from McAfee

So just disable the McAfee on-access scan for the duration of this test.

In Service Explorer, add this file as an attachment to your message

1
Notice the test seems to have been successful, however, our attachment has been deleted.
Look at the trace file –
You will see -
ERROR 13/Oct/2011:15:32:17.968 [168c] message is infected with EICAR test file
ERROR 13/Oct/2011:15:32:17.968 [168c] cannot repair object, mark it for removing.
INFO 13/Oct/2011:15:32:17.968 [168c] remove infected message part 'virusTester.txt'
Full trace -DEBUG 13/Oct/2011:15:32:04.875 [168c] run filter [McAfee Anti-Virus] {
DATA 13/Oct/2011:15:32:04.890 [168c] getting class com.vordel.security.antivirus.McAfeeScanner with classLoader.loadClass()
DATA 13/Oct/2011:15:32:04.890 [168c] loaded class com.vordel.security.antivirus.McAfeeScanner
DEBUG 13/Oct/2011:15:32:04.890 [168c] registered scanner class
DEBUG 13/Oct/2011:15:32:04.890 [168c] data files in D:\Work\envs\OEG\Gateway\enterprisegateway\conf\plugin\mcafee\datv2
DEBUG 13/Oct/2011:15:32:04.890 [168c] using McAfee V2 interface
DEBUG 13/Oct/2011:15:32:04.890 [168c] data file: D:\Work\envs\OEG\Gateway\enterprisegateway\conf\plugin\mcafee\datv2\avvclean.dat
DEBUG 13/Oct/2011:15:32:04.906 [168c] data file: D:\Work\envs\OEG\Gateway\enterprisegateway\conf\plugin\mcafee\datv2\avvnames.dat
DEBUG 13/Oct/2011:15:32:04.906 [168c] data file: D:\Work\envs\OEG\Gateway\enterprisegateway\conf\plugin\mcafee\datv2\avvscan.dat
DEBUG 13/Oct/2011:15:32:04.906 [168c] engine location: D:\Work\envs\OEG\Gateway\enterprisegateway\win32\lib
DEBUG 13/Oct/2011:15:32:08.281 [1a34] opdb commit loop: sleep for max 5000ms
DATA 13/Oct/2011:15:32:08.671 [1368] DataSource after getConnection {numActive = 1, numIdle = 0}
DEBUG 13/Oct/2011:15:32:13.281 [1a34] opdb commit loop: sleep for max 5000ms
DATA 13/Oct/2011:15:32:13.687 [1368] DataSource after getConnection {numActive = 1, numIdle = 0}
DEBUG 13/Oct/2011:15:32:17.796 [168c] AV initialised, support level: AVU_FULLYSUPPORTED
INFO 13/Oct/2011:15:32:17.796 [168c] McAfee scanner initialised.
DEBUG 13/Oct/2011:15:32:17.812 [168c] begin processing compound body 'anonymous' (0 parts)
DATA 13/Oct/2011:15:32:17.812 [168c] snd 0025:
DATA 13/Oct/2011:15:32:17.812 [168c] rcv 746 from max of 1658: <000002d9 --VORDEL-SOAPBOX-MULTIPART-BOUNDARY-0.17758321916921194 Content-Type: text/xml
AMEX
12345678
--VORDEL-SOAPBOX-MULTIPART-BOUNDARY-0.17758321916921194 Content-ID: virusTester.txt Content-Type: text/plain X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* --VORDEL-SOAPBOX-MULTIPART-BOUNDARY-0.17758321916921194-- 0 >
DEBUG 13/Oct/2011:15:32:17.828 [168c] new buffered content factory 06C029F8
DEBUG 13/Oct/2011:15:32:17.828 [168c] buffered content 06C029F8, size=0/4
DATA 13/Oct/2011:15:32:17.828 [168c] getting class com.vordel.dwe.ContentBuffer with classLoader.loadClass()
DATA 13/Oct/2011:15:32:17.828 [168c] loaded class com.vordel.dwe.ContentBuffer
DEBUG 13/Oct/2011:15:32:17.828 [168c] [06C029F8] new chunk 06E87408 from 06E016D8 to 06E01865 (397)
DATA 13/Oct/2011:15:32:17.828 [168c] new content stack 00BB6B98
DATA 13/Oct/2011:15:32:17.828 [168c] push source buffered onto 00BB6B98
DEBUG 13/Oct/2011:15:32:17.828 [168c] handle type text/xml with factory class com.vordel.mime.XMLBody$Factory
DEBUG 13/Oct/2011:15:32:17.843 [168c] new buffered content factory 0AB508B8
DEBUG 13/Oct/2011:15:32:17.843 [168c] buffered content 0AB508B8, size=0/4
DEBUG 13/Oct/2011:15:32:17.843 [168c] [0AB508B8] new chunk 07070EF8 from 00BFA7A8 to 00BFA7EE (70)
DATA 13/Oct/2011:15:32:17.843 [168c] new content stack 00BB6BB0
DATA 13/Oct/2011:15:32:17.843 [168c] push source buffered onto 00BB6BB0
DEBUG 13/Oct/2011:15:32:17.843 [168c] handle type text/plain with factory class com.vordel.mime.Body$1
DEBUG 13/Oct/2011:15:32:17.843 [168c] begin processing body part 'anonymous'
DEBUG 13/Oct/2011:15:32:17.843 [168c] start: buffer() null
DEBUG 13/Oct/2011:15:32:17.843 [168c] start: use new buffer for null
DEBUG 13/Oct/2011:15:32:17.843 [168c] new buffered content factory 06E84B58
DEBUG 13/Oct/2011:15:32:17.843 [168c] buffered content 06E84B58, size=0/4
DEBUG 13/Oct/2011:15:32:17.843 [168c] start: copy to the new buffer for null
DEBUG 13/Oct/2011:15:32:17.859 [168c] new buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.859 [168c] [06E84B58] new chunk 06E44118 from 07060B70 to 07060CFD (397)
DEBUG 13/Oct/2011:15:32:17.859 [168c] delete buffered content stream 0AD771D0
DATA 13/Oct/2011:15:32:17.859 [168c] new content stack 00BB6B80
DATA 13/Oct/2011:15:32:17.859 [168c] push source buffered onto 00BB6B80
DATA 13/Oct/2011:15:32:17.859 [168c] getting class com.vordel.security.antivirus.McAfeeScanner with classLoader.loadClass()
DATA 13/Oct/2011:15:32:17.859 [168c] loaded class com.vordel.security.antivirus.McAfeeScanner
DATA 13/Oct/2011:15:32:17.859 [168c] getting class com.vordel.dwe.NativeContentSource with classLoader.loadClass()
DATA 13/Oct/2011:15:32:17.859 [168c] loaded class com.vordel.dwe.NativeContentSource
DATA 13/Oct/2011:15:32:17.859 [168c] getting class com.vordel.security.antivirus.McAfeeScannerConfig with classLoader.loadClass()
DATA 13/Oct/2011:15:32:17.859 [168c] loaded class com.vordel.security.antivirus.McAfeeScannerConfig
DEBUG 13/Oct/2011:15:32:17.859 [168c] scanner will remove any infected objects.
INFO 13/Oct/2011:15:32:17.859 [168c] Custom scan
DEBUG 13/Oct/2011:15:32:17.859 [168c] AVP_REPAIR
DEBUG 13/Oct/2011:15:32:17.859 [168c] AVP_SERVER
DEBUG 13/Oct/2011:15:32:17.859 [168c] AVP_SCANALLFILES
DEBUG 13/Oct/2011:15:32:17.859 [168c] scan level 3
DEBUG 13/Oct/2011:15:32:17.875 [168c] decompress archives
DEBUG 13/Oct/2011:15:32:17.875 [168c] decompress exes
DEBUG 13/Oct/2011:15:32:17.875 [168c] heuristic program analysis
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0D0CA12C)
DEBUG 13/Oct/2011:15:32:17.875 [168c] deferred IO request AVIORQ_PATHNAME
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.875 [168c] deferred IO request AVIORQ_SIZE
DEBUG 13/Oct/2011:15:32:17.875 [168c] body size: 397
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.875 [168c] deferred IO request AVIORQ_ALTERNATENAME
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.875 [168c] deferred IO request AVIORQ_OPENREAD
DEBUG 13/Oct/2011:15:32:17.875 [168c] new buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.875 [168c] open stream for reading, size 397
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_OBJECTSTART(0x5,00000000)
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_OBJECTSIZE(0x5,0000018D)
DATA 13/Oct/2011:15:32:17.875 [168c] 0D0CB958/AVM_OBJECTNAME(0x5,10C7B05C)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_QUERYDENYSCAN(0x5,00000000)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.890 [168c] deferred IO request AVIORQ_SEEKSTART
DEBUG 13/Oct/2011:15:32:17.890 [168c] set stream position to 0 (forward).
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.890 [168c] deferred IO request AVIORQ_READ
DEBUG 13/Oct/2011:15:32:17.890 [168c] read 397 bytes
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_QUERYQUITSCANNING(0x5,00000000)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_QUERYQUITSCANNING(0x5,00000000)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_OBJECTSUMMARY(0x5,00000000)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_OBJECTCLOSED(0x5,00000000)
DATA 13/Oct/2011:15:32:17.890 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.890 [168c] deferred IO request AVIORQ_CLOSE
DEBUG 13/Oct/2011:15:32:17.890 [168c] delete buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.906 [168c] close stream, size 397
DEBUG 13/Oct/2011:15:32:17.906 [168c] scanner status is [NOVIRUS]
DATA 13/Oct/2011:15:32:17.906 [168c] pop source of type buffered off 00BB6B80
DEBUG 13/Oct/2011:15:32:17.906 [168c] delete buffered content factory 06E84B58
DEBUG 13/Oct/2011:15:32:17.906 [168c] [06E84B58] delete chunk 06E44118 from 07060B70 to 07060CFD (397)
DATA 13/Oct/2011:15:32:17.906 [168c] deleted stack 00BB6B80
DEBUG 13/Oct/2011:15:32:17.906 [168c] finish processing body part 'anonymous'
DEBUG 13/Oct/2011:15:32:17.906 [168c] begin processing body part 'virusTester.txt'
DEBUG 13/Oct/2011:15:32:17.906 [168c] start: buffer() virusTester.txt
DEBUG 13/Oct/2011:15:32:17.906 [168c] start: use new buffer for virusTester.txt
DEBUG 13/Oct/2011:15:32:17.906 [168c] new buffered content factory 06E84B58
DEBUG 13/Oct/2011:15:32:17.906 [168c] buffered content 06E84B58, size=0/4
DEBUG 13/Oct/2011:15:32:17.906 [168c] start: copy to the new buffer for virusTester.txt
DEBUG 13/Oct/2011:15:32:17.921 [168c] new buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.921 [168c] [06E84B58] new chunk 06E43AB0 from 00BCCE80 to 00BCCEC6 (70)
DEBUG 13/Oct/2011:15:32:17.921 [168c] delete buffered content stream 0AD771D0
DATA 13/Oct/2011:15:32:17.921 [168c] new content stack 00BB6B80
DATA 13/Oct/2011:15:32:17.921 [168c] push source buffered onto 00BB6B80
DEBUG 13/Oct/2011:15:32:17.921 [168c] scanner will remove any infected objects.
INFO 13/Oct/2011:15:32:17.921 [168c] Custom scan
DEBUG 13/Oct/2011:15:32:17.921 [168c] AVP_REPAIR
DEBUG 13/Oct/2011:15:32:17.921 [168c] AVP_SERVER
DEBUG 13/Oct/2011:15:32:17.921 [168c] AVP_SCANALLFILES
DEBUG 13/Oct/2011:15:32:17.921 [168c] scan level 3
DEBUG 13/Oct/2011:15:32:17.921 [168c] decompress archives
DEBUG 13/Oct/2011:15:32:17.921 [168c] decompress exes
DEBUG 13/Oct/2011:15:32:17.921 [168c] heuristic program analysis
DATA 13/Oct/2011:15:32:17.921 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0D0CA12C)
DEBUG 13/Oct/2011:15:32:17.937 [168c] deferred IO request AVIORQ_PATHNAME
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.937 [168c] deferred IO request AVIORQ_SIZE
DEBUG 13/Oct/2011:15:32:17.937 [168c] body size: 70
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.937 [168c] deferred IO request AVIORQ_ALTERNATENAME
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.937 [168c] deferred IO request AVIORQ_OPENREAD
DEBUG 13/Oct/2011:15:32:17.937 [168c] new buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.937 [168c] open stream for reading, size 70
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_OBJECTSTART(0x5,00000000)
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_OBJECTSIZE(0x5,00000046)
DATA 13/Oct/2011:15:32:17.937 [168c] 0D0CB958/AVM_OBJECTNAME(0x5,10C7B048)
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_QUERYDENYSCAN(0x5,00000000)
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.953 [168c] deferred IO request AVIORQ_SEEKSTART
DEBUG 13/Oct/2011:15:32:17.953 [168c] set stream position to 0 (forward).
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.953 [168c] deferred IO request AVIORQ_READ
DEBUG 13/Oct/2011:15:32:17.953 [168c] read 70 bytes
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_QUERYQUITSCANNING(0x5,00000000)
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_QUERYQUITSCANNING(0x5,00000000)
DATA 13/Oct/2011:15:32:17.953 [168c] 0D0CB958/AVM_OBJECTINFECTED(0x5,0DEF04F0)
ERROR 13/Oct/2011:15:32:17.968 [168c] message is infected with EICAR test fileDEBUG 13/Oct/2011:15:32:17.968 [168c] callback: scanner status 1
DATA 13/Oct/2011:15:32:17.968 [168c] 0D0CB958/AVM_QUERYDENYREPAIR(0x5,00000000)
DATA 13/Oct/2011:15:32:17.968 [168c] 0D0CB958/AVM_OBJECTNOTREPAIRED(0x5,0000000C)
ERROR 13/Oct/2011:15:32:17.968 [168c] cannot repair object, mark it for removing.
DATA 13/Oct/2011:15:32:17.968 [168c] 0D0CB958/AVM_OBJECTSUMMARY(0x5,00000003)
DATA 13/Oct/2011:15:32:17.968 [168c] 0D0CB958/AVM_OBJECTCLOSED(0x5,00000000)
DATA 13/Oct/2011:15:32:17.968 [168c] 0D0CB958/AVM_IOREQUEST(0x0,0DEF6FE8)
DEBUG 13/Oct/2011:15:32:17.968 [168c] deferred IO request AVIORQ_CLOSE
DEBUG 13/Oct/2011:15:32:17.968 [168c] delete buffered content stream 0AD771D0
DEBUG 13/Oct/2011:15:32:17.968 [168c] close stream, size 70
DEBUG 13/Oct/2011:15:32:17.968 [168c] native: set scanner status to 3
DEBUG 13/Oct/2011:15:32:17.968 [168c] scanner status is [REMOVED]
INFO 13/Oct/2011:15:32:17.968 [168c] remove infected message part 'virusTester.txt'
DATA 13/Oct/2011:15:32:17.984 [168c] pop source of type buffered off 00BB6B80
DEBUG 13/Oct/2011:15:32:17.984 [168c] delete buffered content factory 06E84B58
DEBUG 13/Oct/2011:15:32:17.984 [168c] [06E84B58] delete chunk 06E43AB0 from 00BCCE80 to 00BCCEC6 (70)
DATA 13/Oct/2011:15:32:17.984 [168c] deleted stack 00BB6B80
DEBUG 13/Oct/2011:15:32:17.984 [168c] finish processing body part 'virusTester.txt'
DEBUG 13/Oct/2011:15:32:17.984 [168c] attempt to remove part virusTester.txt
DEBUG 13/Oct/2011:15:32:17.984 [168c] removed part com.vordel.mime.RawBody@13ad88b/virusTester.txt from partsById
DEBUG 13/Oct/2011:15:32:17.984 [168c] removed part com.vordel.mime.RawBody@13ad88b from allParts
DEBUG 13/Oct/2011:15:32:17.984 [168c] finish processing compound body 'anonymous' (1 parts)
DEBUG 13/Oct/2011:15:32:17.984 [168c] } = 1, in 13109 milliseconds
DEBUG 13/Oct/2011:15:32:17.984 [168c] run filter [Reflect message & attributes] {
DEBUG 13/Oct/2011:15:32:18.000 [168c] qa reflecting request
DEBUG 13/Oct/2011:15:32:18.000 [168c] } = 1, in 0 milliseconds
DEBUG 13/Oct/2011:15:32:18.000 [168c] ..."VirusChecker" complete.