http://biemond.blogspot.de/search/label/OWSM
also a BIG thanks to my colleague FlaviusS for the SAMLCredentialMapperProvider setup.
In this scenario, I create a web service and deploy it to WLS server running in nc_domain.
I then create a SOA composite with a BPEL process that calls this service.
The SOA composite is deployed to bpmps6_domain.
A user called wsclient has been created in the WLS ldap of both domains.
Now to SAML -
SAML recognises 3 Roles -
1. the principal aka the user e.g. wsclient
2. the identityProvider e.g. WLS ldap
3. the serviceProvider e.g. the web service running on nc_domain
To quote Wikipedia -
"In the use case addressed by SAML, the principal requests a service from the service provider. The service provider requests and obtains an identity assertion from the identity provider. On the basis of this assertion, the service provider can make an access control decision - in other words it can decide whether to perform some service for the connected principal. Before delivering the identity assertion to the SP, the IdP may request some information from the principal - such as a user name and password - in order to authenticate the principal. SAML specifies the assertions between the three parties: in particular, the messages that assert identity that are passed from the IdP to the SP."
So to recap, I have 2 WLS domains on my laptop -
nc_domain - simple standalone WLS (AdminServer running on port 7005) along with EM and WSM.
bpmps6_domain - SOA PS6 domain with all the bells and whistles!
Keystore setup
I set up the keystores in both domains -
bpmps6 - default-keystore.jks - key is orakey
nc - oracle-keystore.jks - key is orclkey
Now I export the public keys for each and
import the public orakey to nc oracle-keystore.jks
import the public orakey to bpmps6 default-keystore.jks
The cmds -
keytool -genkeypair -keyalg RSA -alias orclkey -keypass
welcome1 -keystore oracle-keystore.jks -storepass welcome1 -validity 3600
keytool -exportcert -alias orclkey -storepass welcome1
-keystore oracle-keystore.jks -file orclServer.cer
keytool -exportcert -alias orakey -storepass welcome1
-keystore default-keystore.jks -file oraServer.der
keytool -import -alias orakey -file oraServer.der -storepass
welcome1 -keystore oracle-keystore.jks
keytool -import -alias orclkey -file orclServer.cer
-storepass welcome1 -keystore default-keystore.jks
keytool -list -storepass welcome1 -keystore
default-keystore.jks
just in case –
Notice I exported the orakey as a .der file - more about that later.
User creation
I create a user called wsclient (password welcome1) on both domains via the WLS console.
btw. passwords don't need to match. However welcome1 is as good a password as any!
SAML CredentialMapperProviderSetup on bpmps6 domain
The use of the key - in this case we point to the oraServer.der file, exported earlier, is specified here -
Opening this, one sees -
When creating this entry, WLS won't accept a .cer file, hence my export to .der format.
Security config in em - bpmps6_domain
sign-csf-key is set to orakey/welcome1
enc-csf-key is set to orakey/welcome1
basic.credentials is set to wsclient/welcome1
keystore-csf-key is set to owsm/welcome1
Security config in em - nc_domain
sign-csf-key is set to orclkey/welcome1
enc-csf-key is set to orclkey/welcome1
keystore-csf-key left to default.
Now to the app itself...
Create the web service
The ws itself is very simple -
You see the policy used is - oracle/wss11_saml_token_with_message_protection_service_policy
Now I deploy this ws to the AdminServer running on nc_domain.
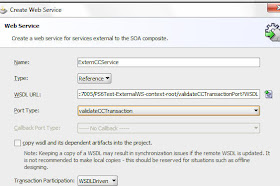
Create the SOA Project
I then create a SOA Project - and include the ws as a reference -
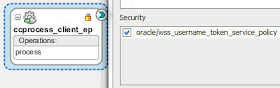
I configure security -
Note: the service policy we defined earlier is
oracle/wss11_saml_token_with_message_protection_service_policy
So the complementary client policy is
oracle/wss11_saml_token_with_message_protection_client_policy
Now I add a simple BPEL process with default input/output parameters.
The process calls the ExternCCservice passing a credit card nr and getting a response (valid/invalid)
I then apply security to the exposed BPEL client -
I deploy the app and test -
Test
Result -




















No comments:
Post a Comment